Introduction In the previous blog post (A Reverse Engineering Walkthrough Journey) we have covered a walkthrough guide to solve the Reverse Engineering challenge written for the NoHat24 security conference. In this blog post, we are going to cover the binary exploitation challenge that involves a custom userland allocator that has been specifically developed for this […]
Introduction This blog post is about a manually Reverse Engineered challenge we have written for this year NoHat24 security conference. The conference was a blast and we also did our best to contribute also with a worskhop on Linux Kernel Fuzzing. The challenge is a compiled C/C++ binary that implements a custom TCP protocol that […]
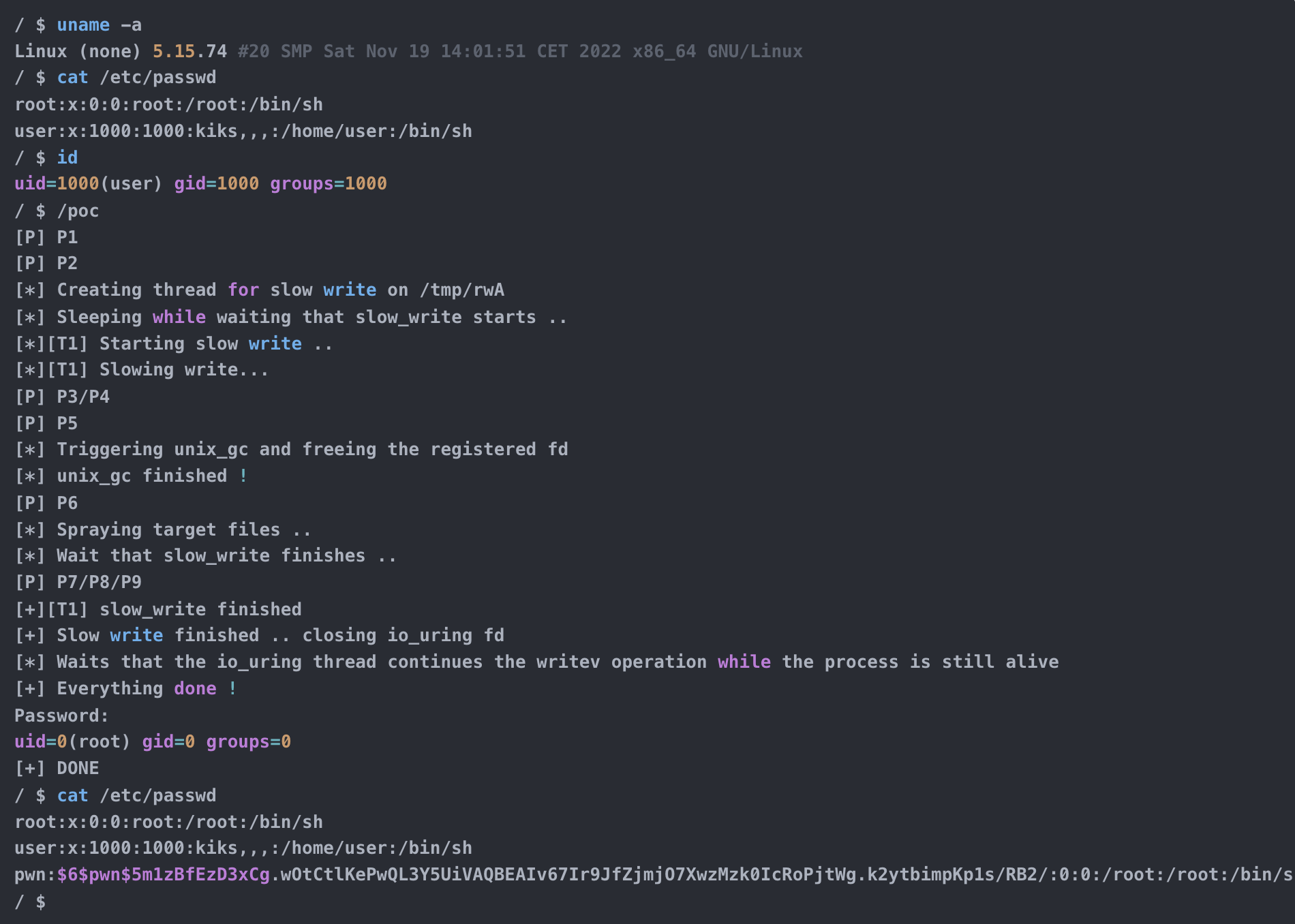
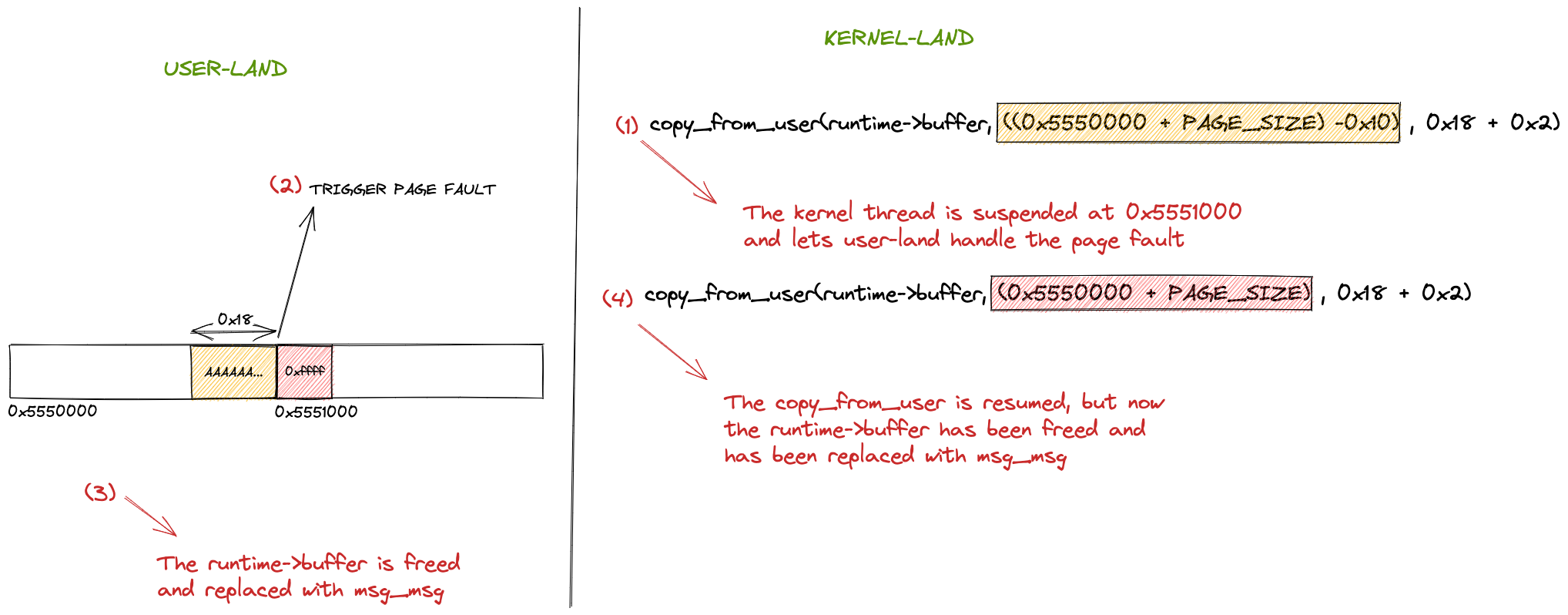
Introduction In the past few weeks, I worked with @LukeGix (checkout his blog post on the same vulnerability here) to exploit the CVE-2022-2602, a very interesting bug from multiple perspectives without a public exploit, that impacts the io_uring subsystem with an Use-After-Free vulnerability handling registered file descriptors.We used a Data-Only attack against kernel version 5.15.74 […]
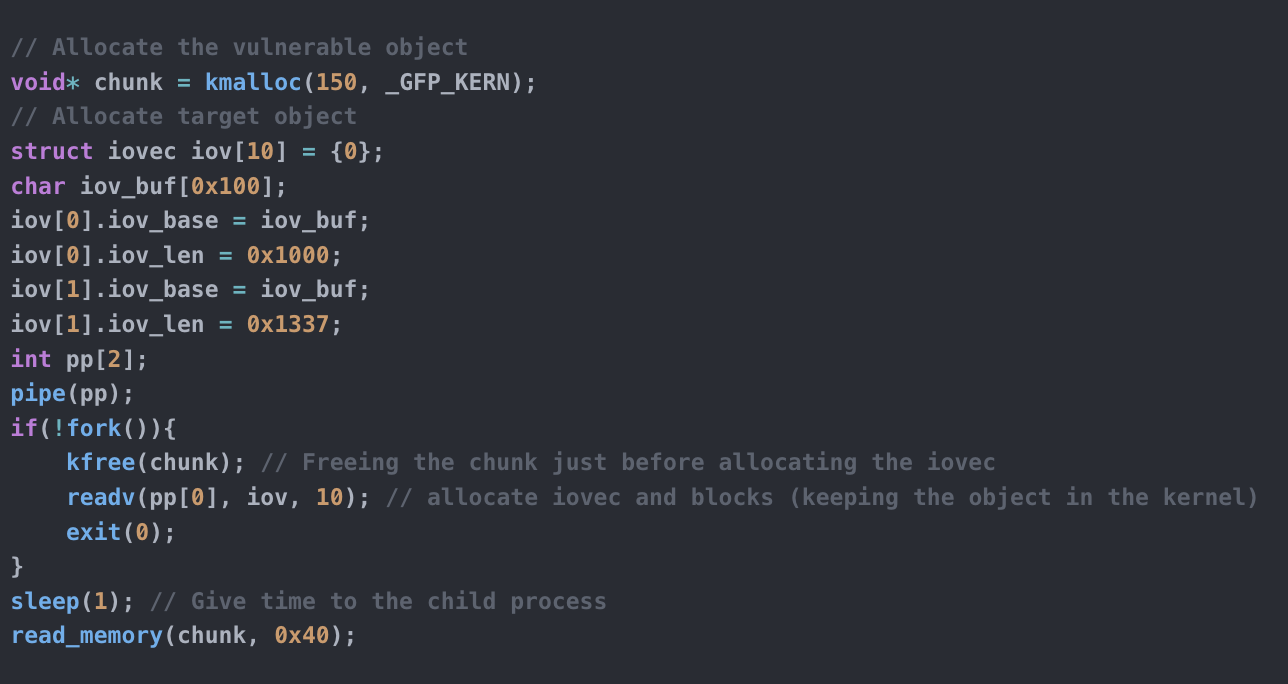
Introduction I was searching for a vulnerability that permitted me to practise what I’ve learned in the last period on Linux Kernel Exploitation with a “real-life” scenario. Since I had a week to dedicate my time in Hacktive Security to deepen a specific argument, I decided to search for a public vulnerability without a public […]
Introduction Github project: https://github.com/kiks7/KRWX During the last few months/year I was studying and approaching the Kernel Exploitation subject and during this journey I developed few tools that assissted me (and currently assist) on better understanding specific topics. Today I want to release my favourine one: KRWX (Kernel Read Write Execute). It is a simple LKM […]
During one of our research activities we discovered several flaws in the ownCloud product.ownCloud is a popular open-source cloud service similar to Google Drive and the last CVE was from the far 2017 (2 years ago).So, we started looking at and we disclosed 3 vulnerabilities related to file sharing, for sure a good attack vector. What we […]
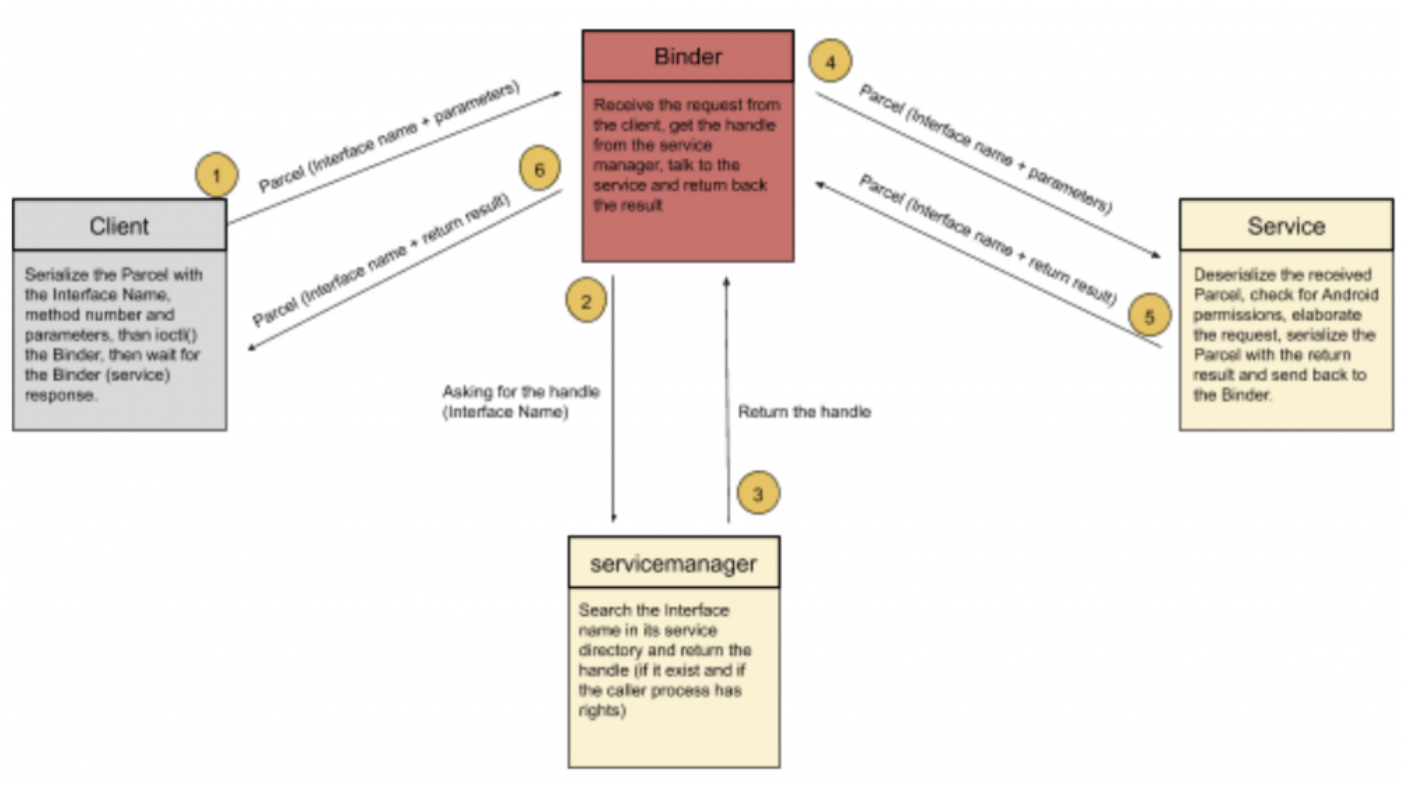
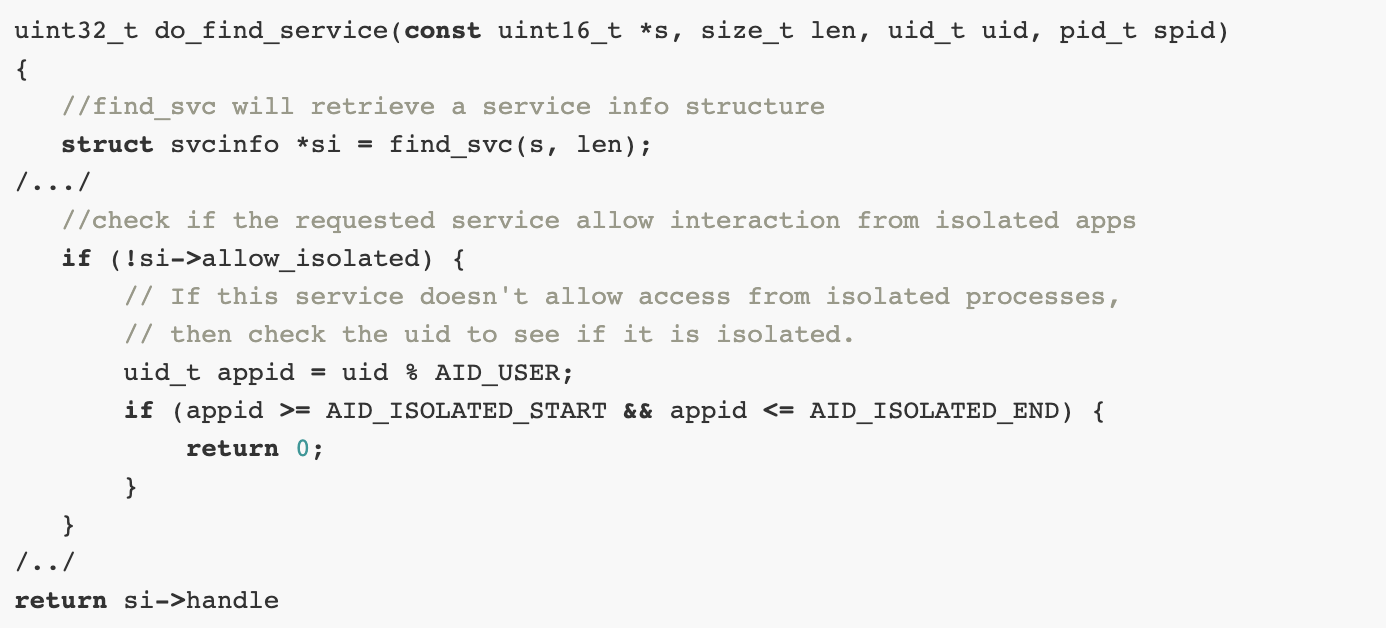
Introduction As mentioned in the previous article, Android uses the Binder for IPC communications. Good to know, the Binder was not created by Google. Its initial appearance was in BeOS, an old OS for mobile devices. After some acquisitions, original developers joined Android and took the Binder with them. The OpenBinder porting to Android was […]
During the time dedicated to research we found 2 Server-Side Request Forgery on Moodle. The first one is a Blind SSRF already discovered in 2018 and tracked as CVE-2018-1042 without a proper patch, the other one is a fresh SSRF while parsing image tags inside the same component (File Picker). They are currently not patched and both […]
Introduction In the last few months I was studying Android Internals in order to perform some security research in the future. I first tried to focus myself in its architecture and fundamentals components, starting from the bootloader stage to the Framework, in order to have an initial high level picture. Then, I focused on the […]
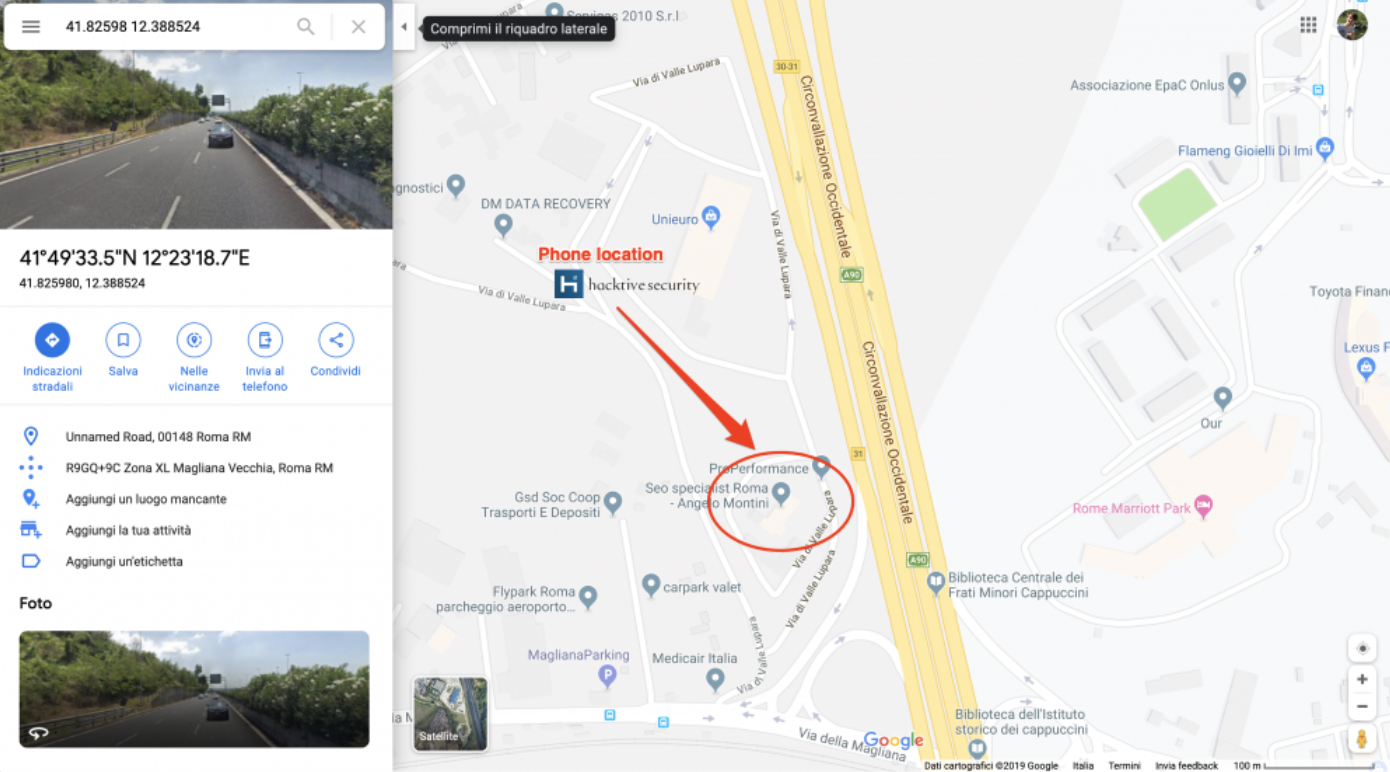
TL;DR During the monthly research activity, in accordance with the relative Respnsible Disclosure program, we found and went in depth with an interesting security issue allowing geolocation of mobile devices using TIM, an Italian communication provider. A malicious user could find the TIM customers geo-position by forcing the approval mechanism to allow the geopositional tracking. By […]
- 1
- 2