Preface As part of our recent research activity, we stumbled upon FormaLMS. The project is an open source Learning Management System built by forma.association and aimed at companies who want a learning platform for internal employees, partners, dealers and sellers. The project is opensource and could be downloaded from the main website: formalms.org and the […]
This is a brief story about how we found a vulnerability on a drupal plugin that, when not configured correctly, could allow an authenticated user to perform a privilege escalation attack on the Drupal platform. This plugin, as stated in the usage section of the drupal website, is used by roughly 522 websites in the […]
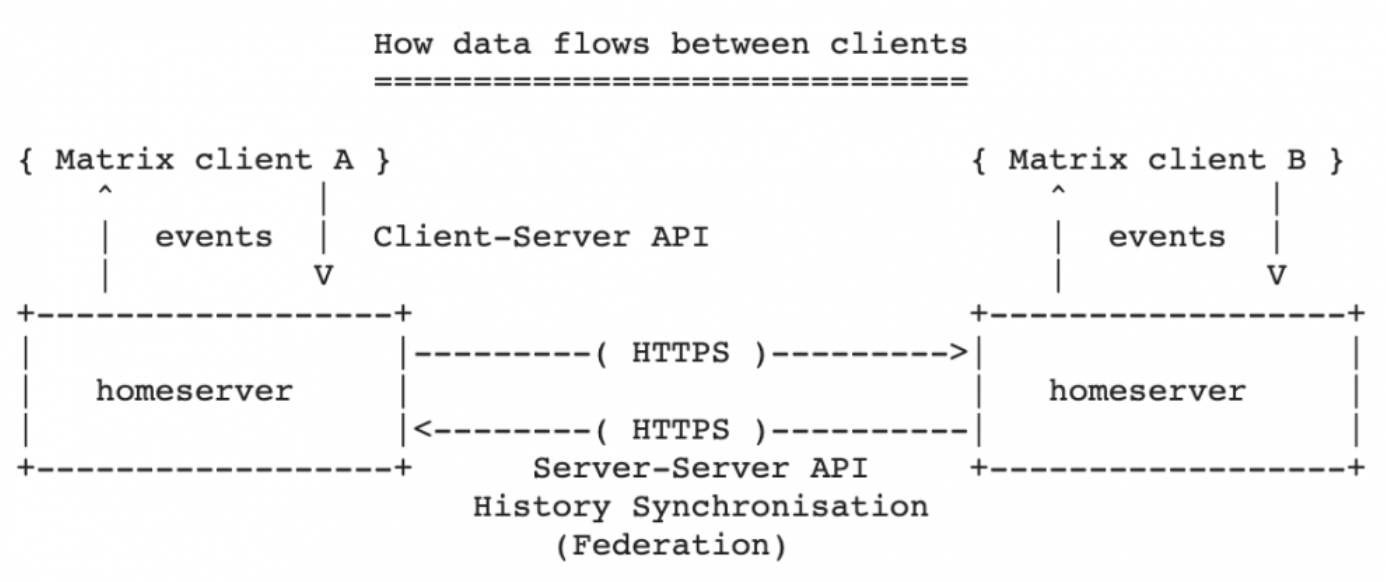
tl;dr The Matrix Synapse servers have been found affected by a security issue about the lack of a validation system for “Server-to-server” API leading to SSRF and Cache poisoning subsequently marked by the team as “feature” or “intended”.In short, a malicious user, if not specifically denied by configuration files, could effectively load malicious content using what is […]
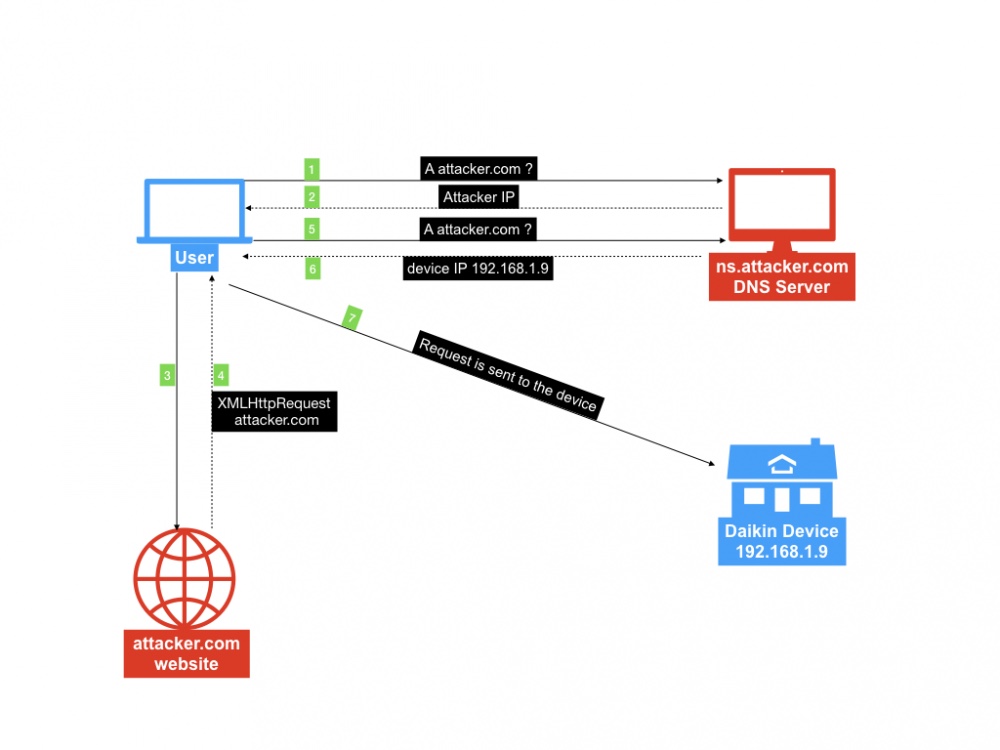
There is a lot of hype around DNS rebinding vulnerability and vulnerable IoT devices, including home cameras, air conditioners or climate control devices; this flaw will cover the lack of origin checking on HTTP requests. DNS Rebinding Attack DNS Rebinding allows an attacker who has control on a DNS server to communicate with a device […]
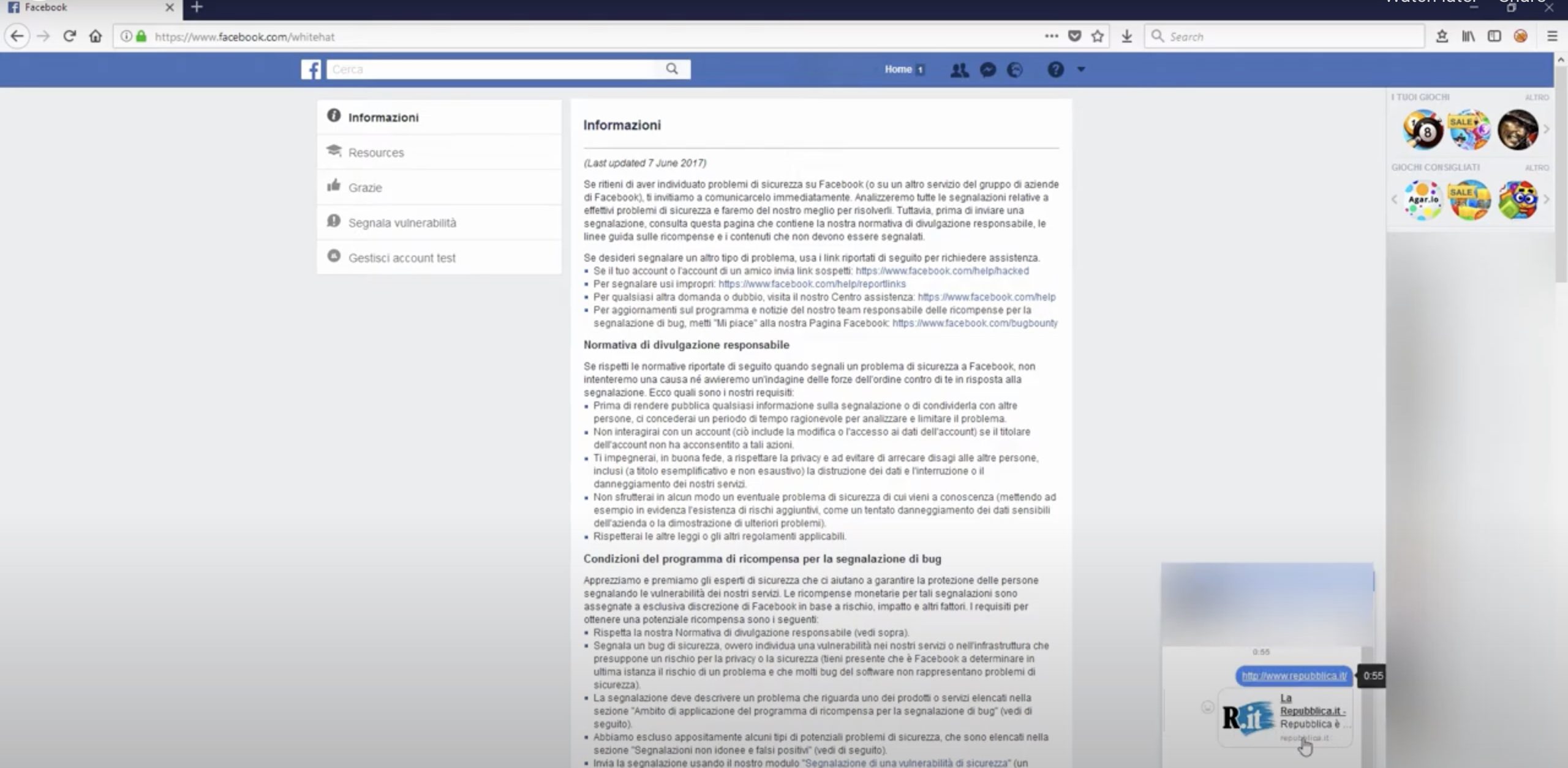
I often wondered how link generation functionality is implemented by major social network applications and, more specifically, the preview generation. Some time ago a friend of mine was spear-phished with a message through the Facebook chat, this happened before Facebook patched the chat application, allowing to exchange of messages only between people connected as friends. […]