TL;DR A Server Side Template Injection in changedetection.io caused by usage of unsafe functions of Jinja2 allows Remote Command Execution on the server host. Update changedetection.io to version 0.45.21 or later. A huge thanks to the mantainer (https://github.com/dgtlmoon) that was very responsive and collaborative to fix the issue, request a CVE number and inform the […]
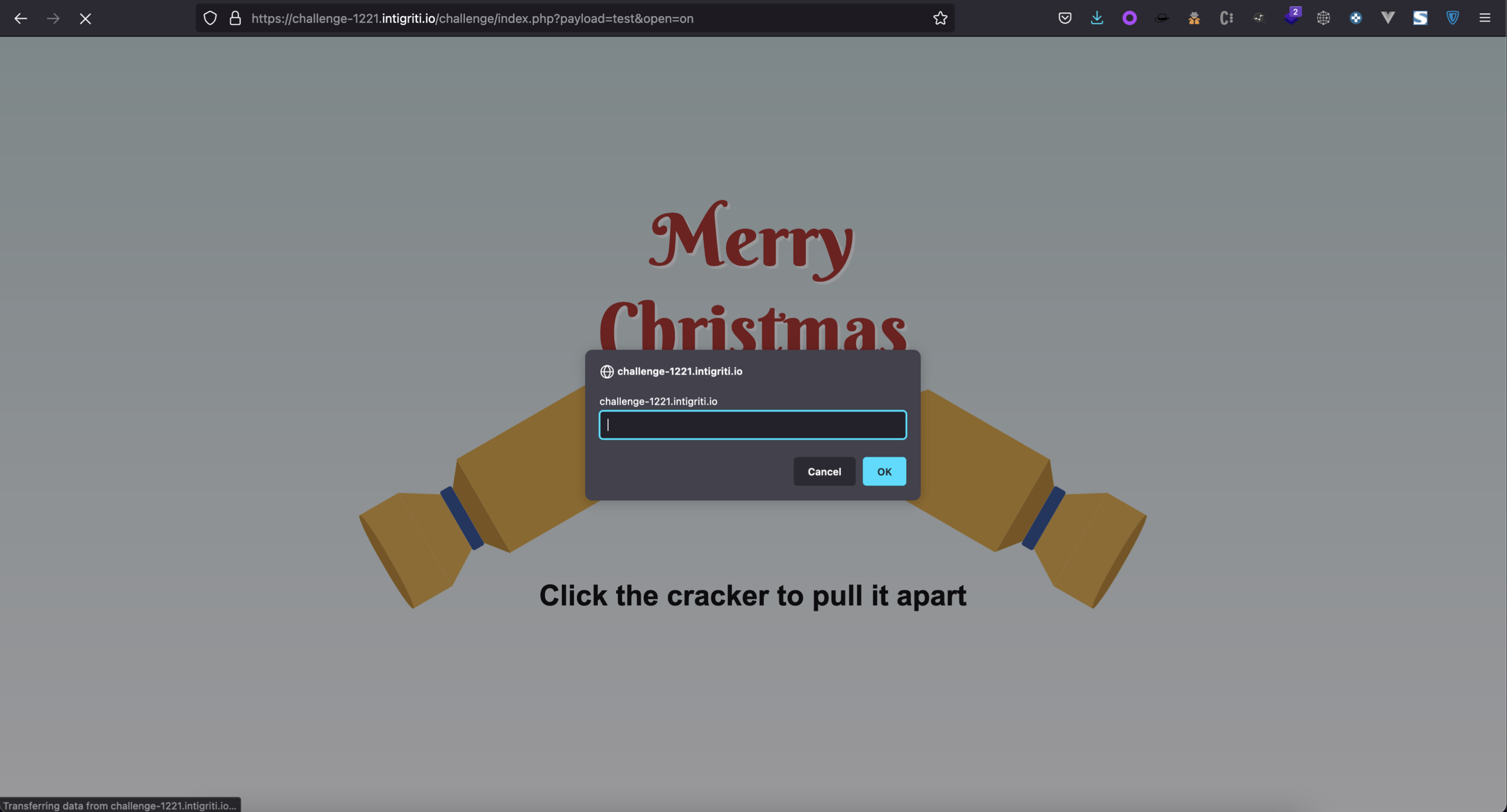
The approach to this challenge was completely different from the past two months, as the vulnerable component was on the backend, forcing us to approach it as a black box scenario. The page presents a simple submittable get form providing the open and payload parameters. To reach that from the UI, a user has to […]
The bug bounty program Intigriti hosts an XSS challenge every month. This time, the challenge was about bypassing CSP by reloading a VueJS instance, getting able to exploit a client side template injection. My solution can be summarized in 4 main steps: Finding reflection and achieving HTML Injection Accessing an abusable piece of code, containing […]
Preface As part of our recent research activity, we stumbled upon FormaLMS. The project is an open source Learning Management System built by forma.association and aimed at companies who want a learning platform for internal employees, partners, dealers and sellers. The project is opensource and could be downloaded from the main website: formalms.org and the […]
This is a brief story about how we found a vulnerability on a drupal plugin that, when not configured correctly, could allow an authenticated user to perform a privilege escalation attack on the Drupal platform. This plugin, as stated in the usage section of the drupal website, is used by roughly 522 websites in the […]
CVE-2020-35749 – Authenticated Directory Traversal Simple Job Board WordPress plugin version < 2.9.3
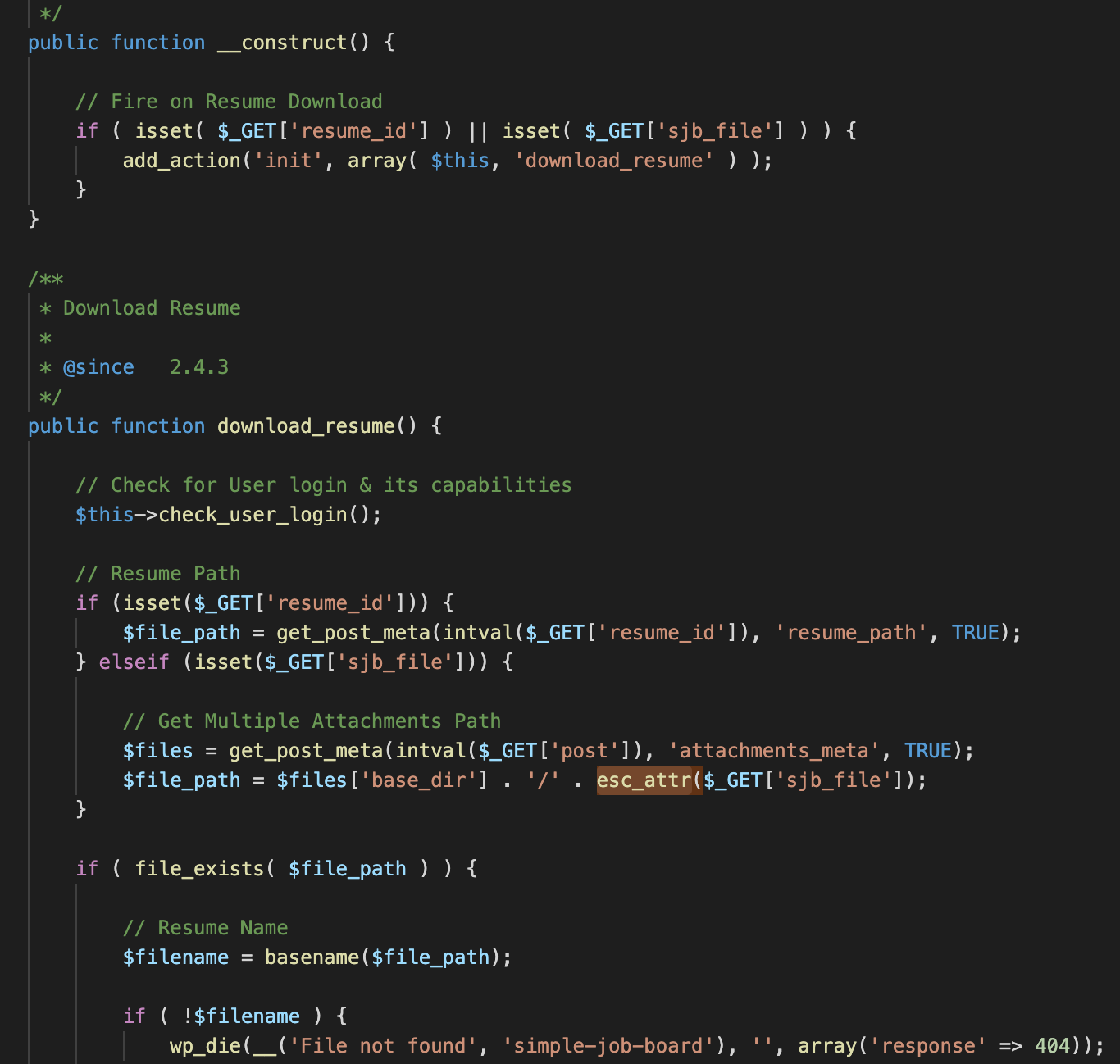
During our research activities we discovered an authenticated local inclusion in the Simple Job Board WordPress plugin. The Simple Job Board WordPress plugin has reached over 20,000 active installations and an excellent reputation in terms of reviews, allowing the simple and efficient management of job offers.[1] Directory traversal allows an attacker to step out of […]
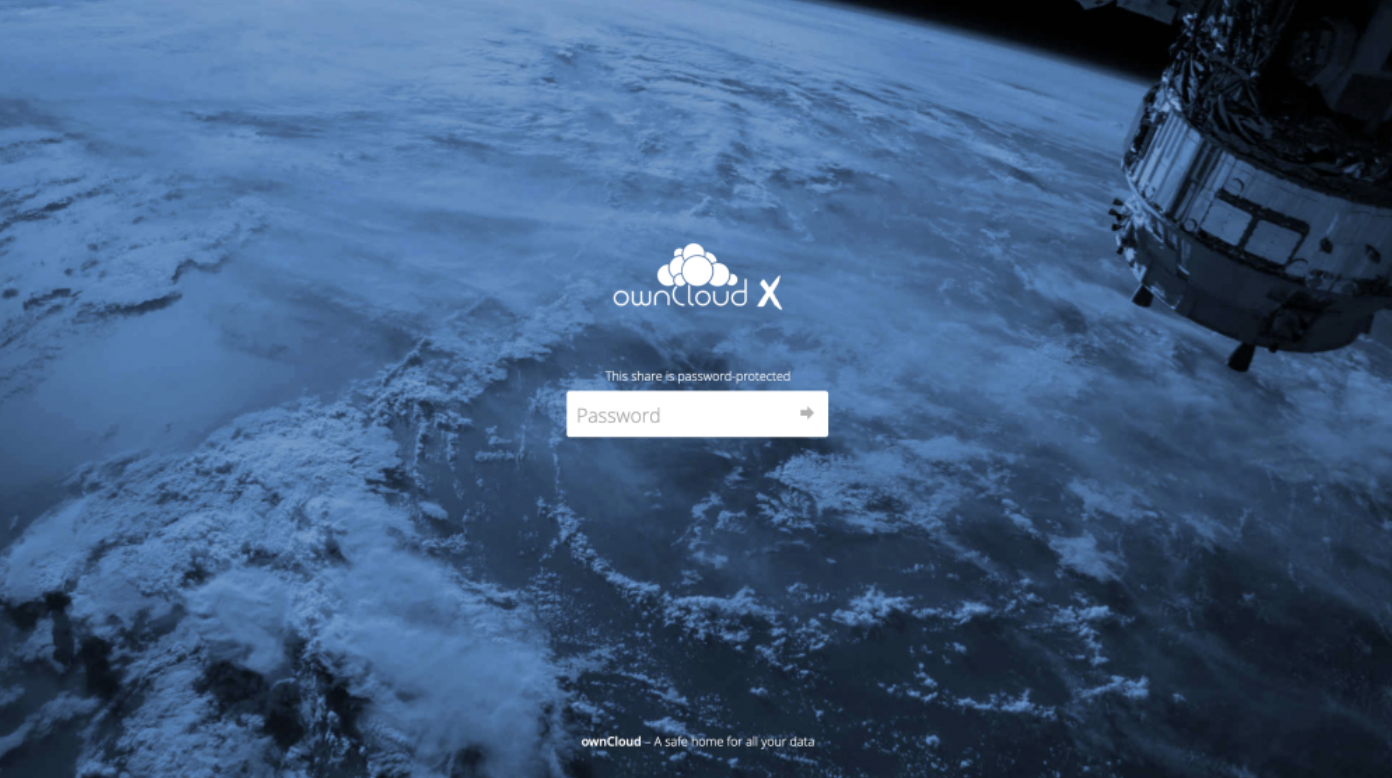
During one of our research activities we discovered several flaws in the ownCloud product.ownCloud is a popular open-source cloud service similar to Google Drive and the last CVE was from the far 2017 (2 years ago).So, we started looking at and we disclosed 3 vulnerabilities related to file sharing, for sure a good attack vector. What we […]
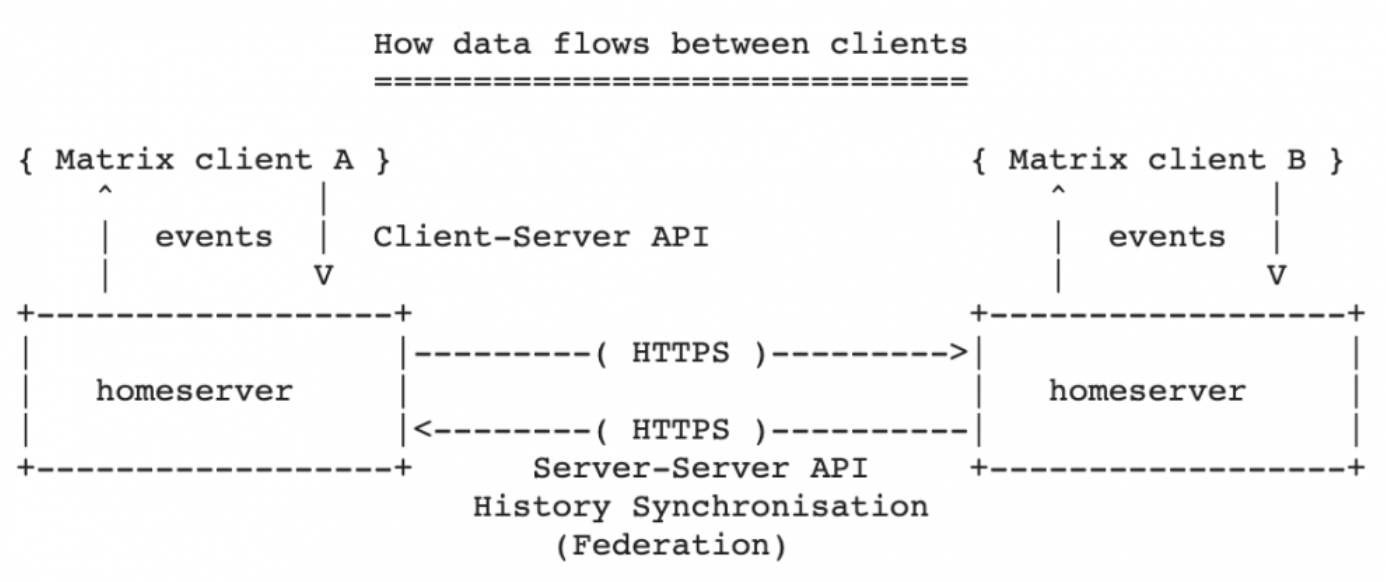
tl;dr The Matrix Synapse servers have been found affected by a security issue about the lack of a validation system for “Server-to-server” API leading to SSRF and Cache poisoning subsequently marked by the team as “feature” or “intended”.In short, a malicious user, if not specifically denied by configuration files, could effectively load malicious content using what is […]
During the time dedicated to research we found 2 Server-Side Request Forgery on Moodle. The first one is a Blind SSRF already discovered in 2018 and tracked as CVE-2018-1042 without a proper patch, the other one is a fresh SSRF while parsing image tags inside the same component (File Picker). They are currently not patched and both […]
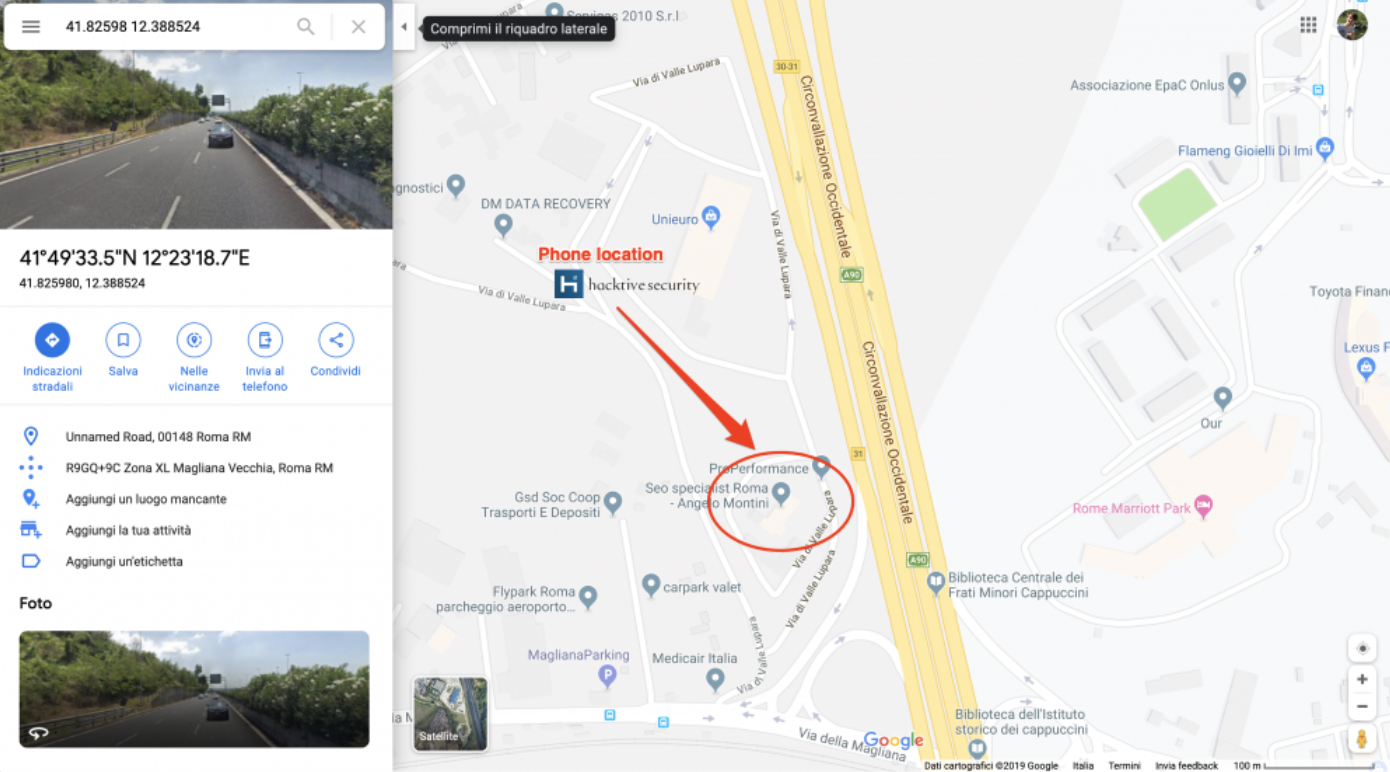
TL;DR During the monthly research activity, in accordance with the relative Respnsible Disclosure program, we found and went in depth with an interesting security issue allowing geolocation of mobile devices using TIM, an Italian communication provider. A malicious user could find the TIM customers geo-position by forcing the approval mechanism to allow the geopositional tracking. By […]
- 1
- 2